
10 December 2025
How Cybercriminals Are Targeting Mobile Users Across South East Asia This Holiday Season

The holiday shopping season is a time of heightened excitement for both consumers and cybercriminals. As consumers increasingly rely on mobile devices for holiday deals, shipping updates and payment confirmation, attackers are seizing the opportunity to strike.
The latest report on mobile shopping from our partners Zimperium reveals a sharp rise in mobile-targeted attacks during peak shopping periods. In this article, we break down Zimperium’s findings, explain why businesses should care, and offer a practical roadmap to protect both employees and enterprise systems from mobile-based threats.
Executive Summary
- Smishing and fake-delivery notifications surged up to 4X during the 2024 holiday season.
- Banking-style malware is expanding to target shopping and payment apps using overlays and accessibility permissions to steal credentials, intercept OTPs, or compromise wallets.
- Legitimate retail apps themselves can be a risk: misconfigured SDKs, hardcoded keys or vulnerable libraries expose users (and enterprises) to remote-code execution or data theft.
- With increasing BYOD (Bring Your Own Device) usage, especially in hybrid and mobile-first workplaces, mobile threats now pose direct risks to corporate systems.
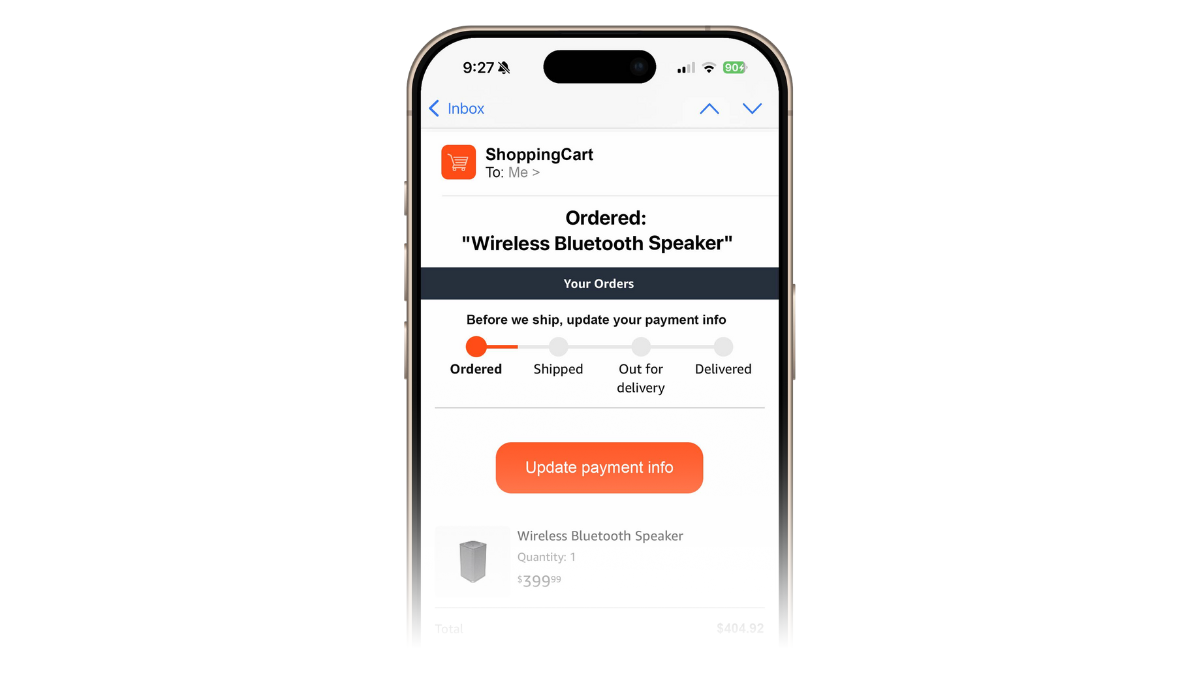
Mishing: The Holiday Phishing Wave
One of the most immediate and widespread threats comes from mishing, i.e. mobile-targeted phishing. Phishing sites tailored for mobile have grown dramatically with 82% of phishing sites examined now specifically targeting mobile devices.
During the 2024 holiday shopping surge, smishing messages and fake delivery notifications masquerading as trusted retailers, courier services or payment platforms increased by as much as fourfold. Attackers employ urgency e.g. “Your package is delayed,” or “Tap here to reschedule delivery” to trick recipients into divulging credentials or installing malicious apps.
For employees using mobile devices for work or personal devices that also access corporate apps, a single click can mean leaking enterprise credentials, bypassing MFA, or enabling broader network compromise. In short, mishing is no longer a consumer-only problem.
Malware Targeting Shopping & Payment Apps
Traditionally, mobile banking trojans focused on banks, but the landscape is shifting. Zimperium’s report shows that malware authors are now targeting shopping and payment apps too, turning consumers’ holiday-shopping convenience into a lucrative attack surface.
These attacks commonly use overlay techniques and abuse accessibility permissions to hijack login screens, capture payment credentials or intercept one-time passwords (OTPs). Digital wallets, instead of just banking apps, are now in scope.
Beyond direct malware, Zimperium notes that counterfeit retail apps, often distributed via third-party stores, fake update prompts, or mishing links, contribute heavily to the risk. Their 2025 dataset identified over 120,000 fake mobile apps, of which 65% impersonate retail or financial brands.
For enterprises with staff purchasing (or even just browsing) holiday-related apps on BYOD or corporate devices, the exposure is very real. Payment data theft, credential reuse for corporate logins, and latent backdoors pose major business threats.
Retail App Vulnerabilities & Supply-Chain Risks
Even legitimate retail apps are not off the hook. The report highlights a variety of systemic flaws: misconfigured SDKs, hardcoded private keys, and vulnerable third-party libraries, all of which can be exploited for remote code execution or data exfiltration.
In many cases, these flaws stem from poor app-development hygiene or weak security controls in the supply chain. During a holiday-driven surge of downloads and new installs, such vulnerabilities become prime ground for attackers.
From an enterprise standpoint, this means that third-party consumer apps, especially those that employees install on their devices, effectively become hidden supply-chain risk vectors. Once compromised, such apps can serve as footholds into enterprise networks or identity systems.
What It Means for South East Asia & Regional Enterprises
South East Asia, with high mobile penetration rates, growing e-commerce adoption and widespread BYOD culture, is particularly exposed. During a holiday surge, everything from shopping apps to courier-tracking tools becomes a potential threat vector.
Many organisations may not treat retail-app security as part of their risk perimeter. Yet as mobile and enterprise ecosystems converge, attackers are increasingly exploiting this overlap. For regional enterprises handling sensitive data or customer information, securing mobile endpoints and applications must be part of a proactive cybersecurity posture.
Recommended Actions: Build a Robust Mobile Security Strategy
Based on Zimperium’s findings, here’s a practical checklist for organisations to consider:
-
Deploy Mobile Threat Defense (MTD) on all managed and BYOD mobile devices to detect phishing, malicious apps, overlays, and runtime exploits.
-
Institute continuous app vetting, especially for third-party retail, courier or payment apps likely to be used by employees. Evaluate SDKs, library dependencies, signing practices and code security.
-
Enforce runtime protection and app attestation for in-house mobile apps to block tampering and protect API communications.
-
Restrict sideloading and untrusted app installation, particularly on work devices. Ensure corporate policies only allow vetted apps.
-
Eliminate hardcoded keys/secrets in apps, rotate credentials, and use secure key management for all distributed apps.
-
Move beyond OTP-based MFA where possible. Given OTP interception is a known vector, consider stronger authentication mechanisms such as hardware or app-based tokens.
-
Conduct regular employee training & awareness programmes focused on phishing, smishing and social-engineering attacks, especially during holiday seasons when shopping-related scams rise.
-
Update incident response plans to account for mobile compromise scenarios, including device takeover and lateral movement from mobile endpoints.
Adopting these measures helps organisations close gaps not just for holiday-season threats, but as part of an ongoing, mobile-centric security strategy.
Why a Managed Security Partner Matters
Given the sophistication and volume of holiday-period mobile threats, many organisations, especially those without specialised security teams, may struggle to stay ahead. A managed security partner brings continuous monitoring, threat intelligence, app-security vetting and rapid incident response, all of which are critical to defending against an increasingly mobile-first threat landscape.
With Vigilant Asia’s expertise in managed security services, organisations in Malaysia and across South East Asia can leverage tailored mobile security strategies to safeguard corporate data, applications and user endpoints without the burden of building and maintaining the infrastructure in-house.
Conclusion
The holiday shopping season brings festive cheer but for cybercriminals, it also presents a golden opportunity. The surge in mishing, malware, and app-supply-chain exploitation shows that mobile threats are evolving rapidly, often blurring the lines between consumer risk and enterprise risk.
For businesses operating in a mobile-first world, especially in regions like South East Asia with high mobile adoption, it’s time to take mobile security seriously. A proactive, layered defense strategy, paired with continuous monitoring and professional support, can help organisations securely navigate the holiday season and beyond.
If you’re interested in mobile security for your organisation, contact us to see how we can help.


